OSI Reference Model stands for Open System Interconnection Reference Model which is used for communication in various networks. The ISO (International organization for standardization) has developed this reference model for communication to be followed worldwide on a given set of a platform. Open system interconnection (OSI) reference model consists of seven layers or seven steps which conclude the overall communication system.
Features of the OSI Model
The various features of the OSI Model are enlisted below:
- Easy to understand the communication over wide networks through the OSI Reference Model architecture.
- Helps to know the details, so that we can get a better understanding of the software and hardware working together.
- Troubleshooting of faults is easier as the network is distributed in seven layers. Each layer has its own functionality, hence the diagnosis of the issue is easy and less time is taken.
- Understanding new technologies generation by generation becomes easier and adaptable with the help of the OSI Model.
1) Layer 1 – Physical layer
- The physical layer is the first and bottom-most layer of the OSI Reference Model.
- It also characterizes the media type, connector type and signal type to be used for communication. Basically, the raw data in the form of bits i.e. 0’s & 1’s are converted into signals and exchanged over this layer. Data encapsulation is also done at this layer. The sender end and the receiving end should be in synchronization and the transmission rate in the form of bits per second is also decided at this layer.
- It provides a transmission interface between the devices and the transmission media and the type of topology to be used for networking along with the type of transmission mode required for transmission is also defined at this level.
- This layer is also identify the interface between the data terminal equipment (DTE) and the data communication equipment (DCE).The services available to the DTE are most often accessed via a modem or channel service unit/data service unit (CSU/DSU).
- Usually, star, bus or ring topologies are used for networking and the modes used are half-duplex, full-duplex or simplex.
2) Layer 2 – Data-link Layer
Data-link layer is the second layer from the bottom of the OSI Reference Model. The main function of the data-link layer is to perform error detection and combine the data bits into frames. It combines the raw data into bytes and bytes to frames and transmits the data packet to the network layer of the desired destination host. At the destination end, the data-link layer receives the signal, decodes it into frames and delivers it to the hardware.
- MAC Address: Data-link layer supervises the physical addressing system called the MAC address for the networks and handles the access of the assorted network components to the physical medium.
The structure of MAC address representing the various fields and bit length can be seen below.
- Error Detection: Only error detection is done at this layer, not error correction. Error correction is done at the Transport layer.
- Sometimes data signals encounter some unwanted signals known as error bits. In order to conquer with the errors, this layer performs error detection. Cyclic Redundancy check (CRC) and checksum are few efficient methods of error checking. We will discuss these in the transport layer functions.
- Flow control & Multiple Access: Data which is sent in the form of a frame between the sender and a receiver over a transmission media at this layer, should transmit and receive at the same pace. When a frame is sent over a medium at a faster speed than the receiver’s working speed, then the data to be received at receiving node will be lost due to a mismatch in speed.
There are two types of flow control process:
Stop and Wait for flow control: In this mechanism, it pushes the sender after the data is transmitted to stop and wait from the receiver's end to get the acknowledgment of the frame received at the receiver end. The second data frame is sent over the medium, only after the first acknowledgment is received, and the process will go on.
Sliding window: In this process, both the sender and the receiver will decide the number of frames after which the acknowledgment should be exchanged. This process is time-saving as fewer resources are used in the flow control process.
- This layer also provisions to provide access to multiple devices to transmit through the same media without collision by using CSMA/CD (carrier sense multiple access/collision detection) protocols.
- Synchronization: Both the devices between which data sharing is taking place should be in synchronization with each other at both the ends so that data transfer can take place smoothly.
- Layer-2 Switches: Layer-2 switches are the devices which forward the data to the next layer on the basis of the physical address (MAC address) of the machine. Firstly it gathers the MAC address of the device on the port on which the frame is to be received and later learns the destination of the MAC address from the address table and forwards the frame to the destination of the next layer.
3) Layer 3 – Network Layer
The network layer is the third layer from the bottom. This layer has the responsibility to accomplish the routing of data packets from the source to destination host between the inter and intra networks operating on the same or different protocols.
- IP Addressing: The IP address is a logical network address and is a 32-bit number which is globally unique for each network host. It principally consists of two parts i.e. network address & host address. It is generally denoted in a dotted-decimal format with four numbers split by dots.
- Routers work at this layer and are used for communication for inter and intra network-wide area networks (WAN’s). Routers who transmit the data packets between the networks do not know the exact destination address of the destination host for which the packet is routed, rather they only know the location of the network to which they belong to and use the information that is stored in the routing table to establish the path along which the packet is to be delivered to the destination. After the packet is delivered to the destination network, it then is delivered to the desired host of that particular network.
4) Layer 4 – Transport Layer
The fourth layer from the bottom is called the transport layer of the OSI Reference model.
(i) This layer is used for an end to end error-free connection between the two different hosts or devices of networks. This is the first one which takes the data from the upper layer i.e. the application layer, and then splits it into smaller packets called the segments and dispenses it to the network layer for further delivery to the destination host.
A host will recognize its peer host at the remote network by its port number.
(ii) The two transport layer protocols include:
- Transmission control protocol (TCP)
- User Datagram Protocol (UDP)
TCP is a connection-oriented and reliable protocol. In this protocol, firstly the connection is established between the two hosts of the remote end, only then the data is sent over the network for communication. The receiver always sends an acknowledgment of the data received or not received by the sender once the first data packet is transmitted.
After receiving the acknowledgment from the receiver, the second data packet is sent over the medium. It also checks the order in which the data is to be received otherwise data is re-transmitted. This layer provides an error correction mechanism and flow control. It also supports client/server model for communication.
UDP is a connection-less and unreliable protocol. Once data is transmitted between two hosts, the receiver host doesn’t send any acknowledgment of receiving the data packets. Thus the sender will keep on sending data without waiting for an acknowledgment.
This makes it very easy to process any network requirement as no time is wasted in waiting for acknowledgment. This type of protocol is widely used in video streaming, online games, video calls, voice over IP where when some data packets of video are lost then it doesn’t have much significance.
(iii) Error Detection & Control: Error checking is provided in this layer because of the following two reasons:
Even if no errors are introduced when a segment is moving over a link, it can be possible for errors to be introduced when a segment is stored in the router’s memory (for queuing). The data link layer is not able to detect an error in this scenario.
There is no assurance that all the links between the source and destination will provide error scrutiny. One of the links may be using a link layer protocol which doesn’t offer the desired outcomes.
The methods used for error check and control are CRC (cyclic redundancy check) and checksum.
CRC: The concept of CRC (Cyclic Redundancy Check) grounds on the binary division of the data component, as the remainder of which (CRC) is appended to the data component and sent to the receiver. The recipient divides data component by an identical divisor.
If the remainder comes up to zero then the data component is allowed to pass to forward the protocol, else, it is assumed that the data unit has been distorted in transmission and the packet is discarded.
Checksum Generator & checker: In this method, the sender uses the checksum generator mechanism in which initially the data component is split into equal segments of n bits. Then, all the segments are added together by employing 1’s complement.
5) Layer 5 – Session Layer
This layer permits the users of different platforms to set up an active communication session between themselves.
The main function of this layer is to provide sync in the dialogue between the two distinctive applications. The synchronization is necessary for efficient delivery of data without any loss at the receiver end.
6) Layer 6 – Presentation Layer
The presentation layer will present the data to its end users in the form in which it can easily be understood. Hence, this layer takes care of the syntax, as the mode of communication used by the sender and receiver may be different.
The data which is in the form of characters and numbers are split into bits before transmission by the layer. It translates the data for networks in the form in which they require it and for devices like phones, PC, etc in the format they require it.
The layer also performs data encryption at the sender's end and data decryption at the receiver's end.
It also performs data compression for multimedia data before transmitting, as the length of multimedia data is very big and much bandwidth will be required to transmit it over media, this data is compressed into small packets and at the receiver's end, it will be decompressed to get the original length of data in its own format.
7) Layer 1– Application Layer
This is the topmost and seventh layer of the OSI reference model. This layer will communicate with the end users & user applications.
This layer grants a direct interface and access to the users with the network. The users can directly access the network at this layer. Few Examples of services provided by this layer include e-mail, sharing data files, FTP GUI based software like Netnumen, Filezilla (used for file sharing), telnet network devices etc.
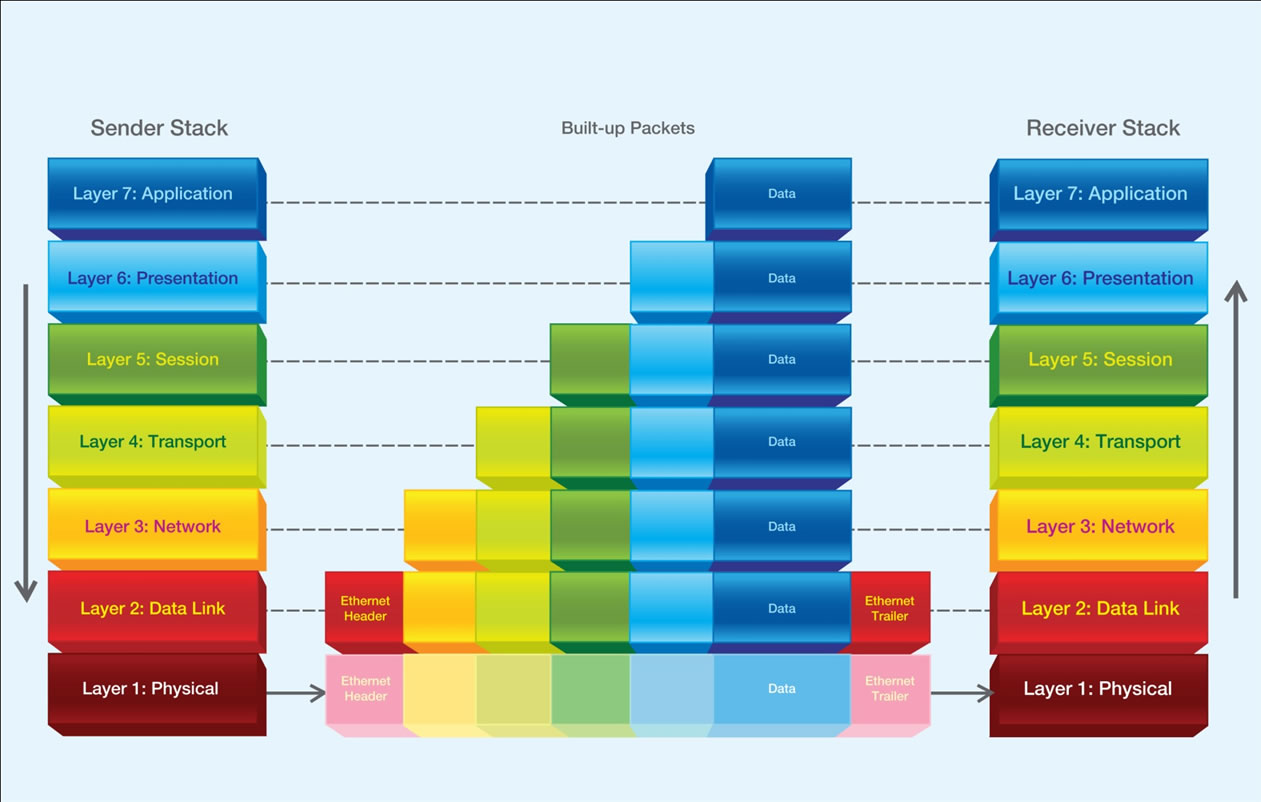
Let’s see how each layer in the OSI reference model communicates with one another with the help of the below diagram.
Enlisted below is the expansion of each Protocol unit exchanged between the layers:
- APDU– Application protocol data unit.
- PPDU– Presentation protocol data unit.
- SPDU– Session protocol data unit.
- TPDU– Transport protocol data unit (Segment).
- Packet– Network layer host-router protocol.
- Frame– Data-link layer host-router protocol.
- Bits– Physical layer host-router protocol.
Data Encapsulation and de-encapsulation
The terms encapsulation and de-encapsulation refer to a process in which protocol information is added to the data and removed from the data when it passes through the layers.
Protocol information can be added before and after the data. If information is added before the data, it is known as a header. If information is added after the data, it is known as a trailer.
Upper layer (Application layer in TCP/IP) or layers (Application, Presentation, and Session layers in OSI) create data stream and handed it down to the Transport layer.
Upper layers don’t use header and trailer with data. But if required, the application that initiates the connection can add header and trailer with data. Since the use of header and trailer in upper layers is application-specific, in encapsulation diagram and terms encapsulated data in upper layers is commonly referred to as the data.
Segment
Transport layer breaks the received data from the upper layers into smaller pieces. Next, it creates a header for each data piece. This header contains all necessary information about the piece that the transport layer in remote host needs to reassemble the data stream back from the pieces. Once the header is attached, the data piece is referred to as segment. Once segments are created, they are handed down to the network layer for further processing.
Packet
Network layer creates a header for each received segment from Transport layer. This header contains information that is required for addressing and routing such as source software address and destination software address. Once this header is attached, the segment is referred to as a packet. Packets are handed down to the Data link layer.
In TCP/IP model the term packet is mentioned as the term datagram. Both terms packet and datagram refer to the same data package. This data package contains a Network layer header and an encapsulated segment.
Frame
Data Link layer receives packets from Network layer. Unlike Transport layer and Network layer which only create a header, it also creates a trailer with a header for each received packet. The header contains information that is required for switching such as source hardware address and destination hardware address. The trailer contains information that is required to detect and drop corrupt data packages in the earliest stage of de-encapsulation. Once the header and trailer are attached with a packet, it is referred to as a frame. Frames are passed down to the Physical layer.
Bits
Physical layer receives frames from Data link layer and converts them into a format that the attached media can carry i.e. for copper wire Physical layer will convert frames in voltages. And if the host is connected with a wireless network, the Physical layer will convert them in radio signals.